Methods for Multicast Key-Capacity
A means of protecting a multi-source multi-terminal noiseless network, with key-dissemination in which secret key K is multicasted from the network sources to its terminals.
A key-dissemination communication protocol is one in which a key K, which is at times secret, is shared among a collection of users as a prelude to future communication tasks requiring shared user common knowledge.
This work initiates the study of key-dissemination in the context of noiseless networks. For a multi-source, multi-terminal network, in the key-dissemination problem one wishes to multicast a key K of rate R for a collection of sources to a collection of terminal nodes. Unlike traditional forms of secure multicast, there is no requirement on K beyond the following three constraints. First, K should be delivered to all terminal nodes, second, K should not be revealed to an eavesdropper with predefined eavesdropping capabilities, and third, K is uniform and has rate at least R. Allowing the shared key K to be any function of the source information grants a flexibility to the communication process.
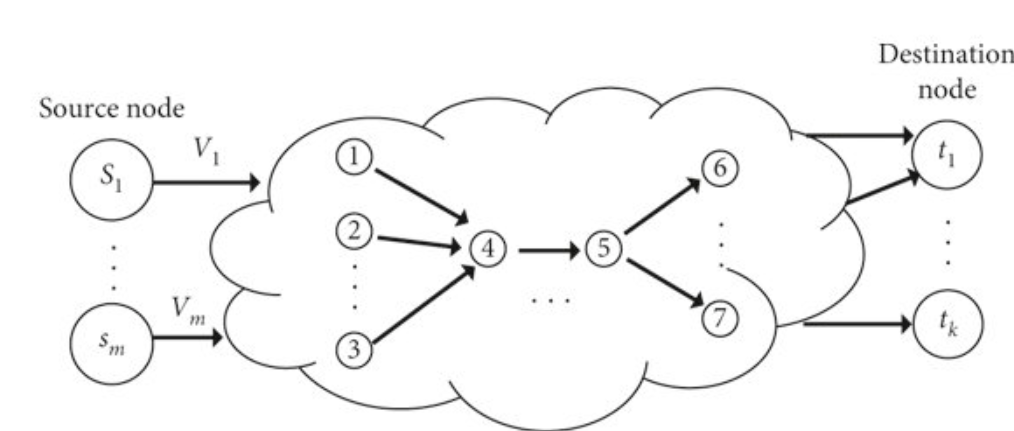
Increased key-rates when compared to traditional secure multicast, while still maintaining similar levels of protection from eavesdroppers.
This scenario may be appropriate for network protocols that share a secret key between a pair of users to later be used as a one-time-pad for the secure communication of sensitive information.
US Provisional Patent Application 63/306,178 filed 2/3/2022.
TRL 3
Available for license or collaboration.
Patent Information:
| App Type |
Country |
Serial No. |
Patent No. |
Patent Status |
File Date |
Issued Date |
Expire Date |
|